cybersecurity services
overview
What is our cybersecurity services?
Cybersecurity is one of the core service lines within CompNet Federal Solutions, inc (CFSI) and our company’s security service portfolio covers the full landscape of information security needs of our clients. We have the very best information security resources in the business that have supported just about every industry imaginable.
0+
0
0%
0countries
024/7
Cybersecurity is one of the core service lines within CompNet Federal Solutions, inc (CFSI) and our company’s security service portfolio covers the full landscape of information security needs of our clients. We have the very best information security resources in the business that have supported just about every industry imaginable. We are currently supporting the DOD, DHS, US Mind, the NRC, the IRS and DOS with their incident response, threat hunting, information security, security validation, FEDRAMP compliance, cloud security and vulnerability management objectives. In addition, CFSI was proudly selected as a prime cybersecurity provider for Navy SPAWAR. We have offerings in all aspects of information security such as penetration testing, enterprise security architecture, security policy development, implementation services and federated identity management; furthermore, we have specialized abilities in security automation, threat hunting and applied threat intelligence and experience implementing the NIST Cybersecurity Framework (CSF) for hybrid and traditionally structured enterprises.
Security Automation Adoption Service

The Need For Speed: Automated malware attacks like WannaCry, NotPetya and as far back as SQL Slammer (2003) spread globally and were executed at a phenomenal rate, nearing machine speed (near light speed). If some attacks have spread across the entire globe in under 10 minutes, how much of our network can be compromised while our Change Control Boards are consulted for approved responses? The answer, “All of it”. CFSI security practitioners are experts at categorizing your own incident response tactics into groups that:
Can be fully automated – repetitive, error prone tasks such as creating and updating trouble tickets, sending notifications, patching and checking patch compliance
- Can benefit from human triggered automation – automated courses of action that can be triggered after an operator has picked the appropriate course of action to run – such as immediately quarantining malware, automatically stopping an identified attack or instantly stopping record theft in process
- Are not appropriate for automation – but can benefit from automated data enrichment, meaning decision support tools will be automated so decisions can be reached quickly and with confidence
- Once the categorization is complete, we design, build, test and implement the new capabilities (complete with training and on demand 24×7 support). We also have services for operating the Automated Courses Of Actions (ACOA) as a service – AaaS. The end result is incredibly faster containment of attacks and malware spread and is more time for your analysts to work security-related tasks rather than administrative tasks.
Applied Threatelligence© (Operationally Applied Threat Intelligence)
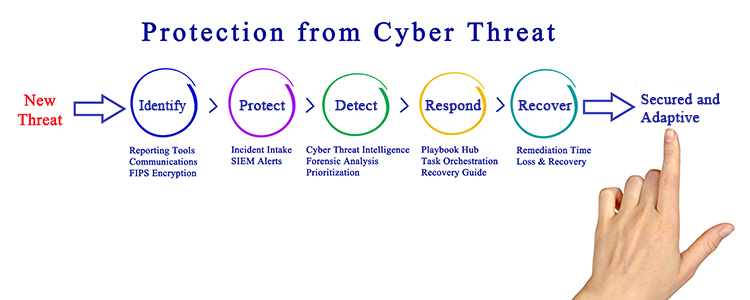
Threat Intelligence shines a light in the darkness when it comes to knowing your enemy. But few organizations know how to make a tangible difference in their security with Threat Intelligence. CFSI’s Threatelligent© offerings monitor and consolidate threat feeds to find the adversaries that can hurt you severely. They also apply that information directly to your individual operations and tool sets and give you very specific directions on what to do to protect your organization. These services not only make you more secure but also serve as excellent sources of budget justification. CFSI will tell you where you should spend your funds and how to cover yourself in areas where you do not yet have sufficient defensive capabilities. These offerings are also one of the inputs to the CFSI Intelligence Driven Threat Hunting service. All CFSI offerings are available as services or as Turn-Key deliverable.
Threatelligent Hunting©: CFSI Intelligence-Driven Threat Hunting (BIT Hunting©)
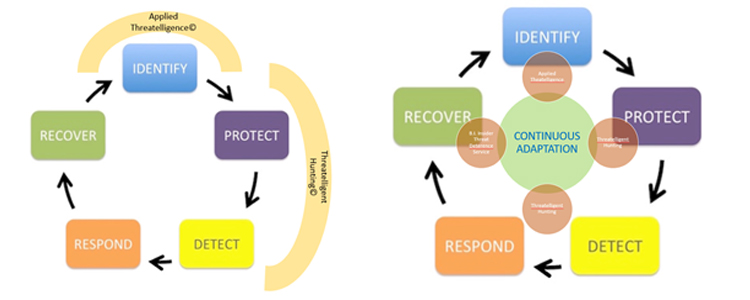
The Best Detection Tools Don’t Matter Without Threat Hunting. Would you build a dome around a city as the only measure to keep mosquitoes out? No. Because some mosquitoes are already living inside, and there are other vectors like rivers that allow them in. So even a perfect perimeter detection and prevention capability – if there were one – is not enough (and there is not one). It is imperative to continue looking for what is already there and what has come in using unexpected vectors. CFSI’s Threatelligent© Hunting (BIT Hunting©) integrates into your security operations processes and is fed by your tools and logs, as well as by the Threat Intelligence feeds that are available in your environment. The CFSI Threatelligent Hunting© solution is also equipped to feed directly to your security infrastructure, meaning that as soon as a new vector of attack, malware component or vulnerability is discovered, your defenses will be updated to keep that from happening in the future. BIT Hunting© is available as a service or as a Turn-Key deliverable.
SOC Optimization Service – Detect, Protect and Correct – Global Best practices
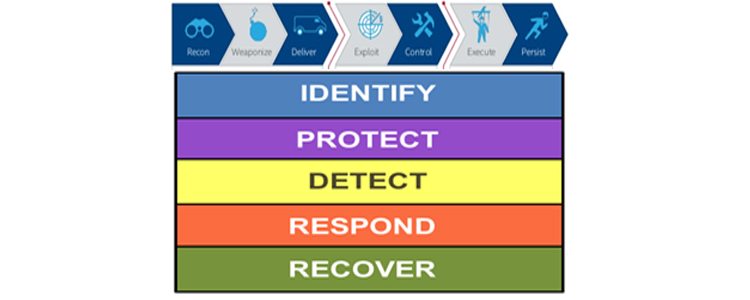
CFSI’s SOC Optimization Service is a consulting offering that leverages expertise in the world’s leading models for Security Operations, such as the NIST Cybersecurity Framework, the ISD 35, the CIS 20 and others in order to evaluate your organization for areas of increased effectiveness and reduced costs. We align our recommendations with the cyber kill chain steps and provide a plan that will take your organization from current state to optimal state. We also synchronize the roll-out timeline to your budget and priorities, whether those priorities come from our Threat Intelligence Service recommendations or from your own leadership. If needed, CFSI also offers delivery options that offload the majority of SOC Transformation duties from your staff, allowing them to continue normal duties while our experts set up your new Information Security capabilities and processes. Our staff will train and support your staff in transitioning to the Turn-Key new SOC tools and methods, or they can remain in place as long as needed.
Insider Threat Deterrence Program – Detect protect and Correct cycle

CFSI followed the US Department of Defense’s DOD and Department of Homeland Security DHS recommendation that DETERRENCE needs to be part of a total cybersecurity strategy and developed a first of its kind approach to stopping insider threat issues with a very cost effective, largely automated solution that complies with the most strict privacy laws, including those going into effect May 25, 2018 via the General Data Protection Regulation (GDPR) regulations in Europe.
This program integrates with many specialty commercial tools and open source software packages and can be stood up in as little as 3 months. The nature of this program keeps us from publicly describing it. But for confidential details on how this offering works, please contact the CFSI Cybersecurity team at 202-304-1501.
Personnel Certifications:
PMP – Project Management Professional
ITIL – Information Technology Infrastructure Library
ISC2 Certifications:
CISSP- Certified Information Systems Security Professional
CCFP- Certified Cyber Forensics Professional
CCSP- Certified Cloud Security Professional
SANS Certifications:
GIAC- Global Information Assurance Certification
GCED- Global Certified Enterprise Defender
GCFA- Global Certified Forensic Analyst
GPEN- Global penetration testing certification
GWAPT- Global Web Application Penetration Tester
GCFE- Global Certified Forensic Examiner
GSNA- Global Systems and Network Auditor
GPPA- Global Perimeter Protection Analyst
GAWN- Global Assessing and Auditing Wireless Networks
GWEB- Global Web Application Defender
GNFA – Network forensic analyst certification
GREM – Reverse Engineering Malware
GXPN – Exploit Researcher and Advanced Penetration Tester
GIAC – Continuous Monitoring Certification (GMON)
GCIH – Incident Handler Certification
Microsoft Certifications
Microsoft Technology Associate ( MTA )
Microsoft Certified Solutions Associate (MCSA)
Microsoft Certified Solutions Expert (MCSE)
Microsoft Certified Solutions Developer (MCSD)
Certified MCITP (Microsoft Certified IT Professional) – Database Administration: 2008
MCSA – Microsoft Certified System Associate in SQL Server 2012
Certified SSRS (SQL Server Reporting Services)
Certified on IIS – Administration
Microsoft SQL Server database
MySQL Database Administrator
Cisco Certifications:
CCNA- Cisco Certified Network Associate
CCNP- Cisco Certified Network Professional
CCIE Security- Cisco Certified Internetwork Expert Security
EC Council Certifications:
CEH – Certified Ethical Hacker
CHFI- Computer Hacking Forensics Investigator
ENSA – EC-Council Network Security Administrator (ENSA}
CNDA- Certified Network Defense Architect c
ECSS- EC-COUNCIL CERTIFIED SECURITY SPECIALIST
ECSP- EC-Council Certified Secure Programmer
ECES- EC-Council Certified Encryption Specialist
LPT – EC Council Licensed Penetration Tester
ECSA- EC-Council Certified Security Analyst
ECIH – EC-Council Certified Incident Handler (ECIH)
CERT CSIH – CERT-Certified Computer Security Incident Handler (CSIH)
Offensive Security: OSCP, OSCE, OSWP and OSEE
EnCase: EnCE
Dod 8570: IAT L2, CNDSP Analyst or IR
Carnegie Mellon: SEI, CCSIH
Oracle Certification:
Oracle Certified Junior Associate (OCJA)
Oracle Certified Associate (OCA)
Oracle Certified Professional (OCP)
Oracle Certified Master (OCM)
Oracle Certified Expert (OCE)
Oracle Certified Specialist (OCS).
Oracle Database 12c Administrator
Oracle SQL and PL/SQL
Oracle MySQL Database Administration
Oracle Data Warehousing
CompTIA Certification:
CompTIA Security +, Network+, Server +, A+, Network+, Server +, Lenix+
CSCIP/G – Certified Smart Card Industry Professional
CSEIP – Certified Smart Card Engineer ICAM Professional
PSP – Physical Security Professional
Solutions
Comprehensive IT services include
Benefits
Our services provide a unique range of benefits
Stop wasting time and money on technology. Let’s get started
